The website uses cookies to deliver services in accordance with the Cookies Policy. You can define the conditions for storing or accessing the cookie mechanism in your browser.

Cylance® Optics
Cylance Optics enables security operations centers (SOC) and security analysts to detect early signs of a breach so that containment responses can be initiated quickly to minimize damage. Cylance Optics also arms analysts with the threat hunting and root cause analysis tools they need to distinguish the subtle signals of a threat from the random noise of routine activity.
Why choose Cylance Optics?
CLOUD-ENABLED—NOT CLOUD-DEPENDENT
Cloud-based Cylance Optics provides monitoring and visibility that span your entire organization, enabling detection and threat hunting for both online and offline devices.
QUICKLY DETECT AND RESPOND TO RANSOMWARE
Ready to move beyond attack visibility? Cylance AI-driven security proactively detects and automates response capabilities. So you can find and neutralize advanced cyberthreats in milliseconds—not hours or days.
PREVENT WIDESPREAD INCIDENTS WITH MACHINE LEARNING
Cylance Optics mitigates and contains threats at the endpoints—drastically minimizing your attack surface and potential lateral movement. So your SOC teams have more time to perform essential duties, instead of monitoring and re-imaging compromised endpoints.
CUSTOM AUTOMATED RESPONSES
Cylance Optics has a built-in playbook with automated incident responses to mitigate endpoint threats. As it automatically collects relevant security information for hunting and forensic analysis, you’ll save your SOC analysts some time.
UNCONSTRAINED THREAT HUNTING
Our advanced, intuitive querying capabilities with Query language objects are purpose-built for MITRE ATT&CK®. It’s designed to enable deep insight for threat hunting and forensics with superior data retention packages—30 days out of the box and up to 365 days.
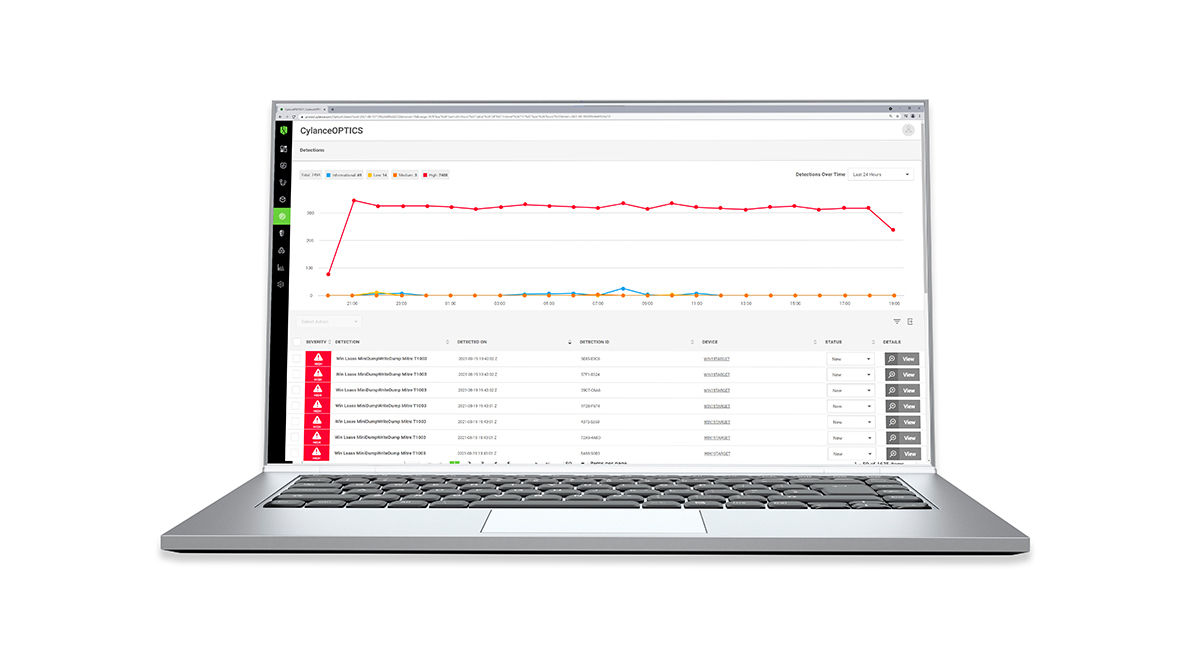
Ceylance Optics is the right fit for organizations that want to:
- Reduce MTTD and MTTR by containing threats with on-demand packages and automated playbooks.
- Remediate threats by rapidly restoring compromised systems to a pristine state.
- Search endpoint data for files, executables, MITRE ATT&CK objects, and other indicators of compromise.
- Protect endpoints without imposing performance bottlenecks.
- Quickly identify the signals of an attack hidden within masses of endpoint data.
- Increase their resilience by streamlining threat hunting and root cause analysis.
IT solutions
Test a product
On local martkets Bakotech Group operates through a well-established partner network, including over 1,000 active dealers. Key IT-integrators and are involved in the realization of large-scale projects concerning implementing solutions for end-customers from various segments of business. Bakotech's business strategy is True Value Added Distribution or in other words - project oriented distribution.
We are providing our partners with a wide range of services such as PR, co-marketing activities, pre post-sales support, trainings for partners and end-customers, PoC, PoV, solution consulting, implementation support and technical support.
Contact Us
Bakotech Sp. z o.o.
Dane firmy
VAT ID 6762466740
REGON 122894922
KRS 0000467615
Kontakt
ph. +48 12 340 90 30












