Pin-point accuracy using behavior analytics
Your current VAM depends too heavily upon version checking.
It may flag secure hosts as risks due to old version numbers.
It will fail to flag insecure hosts that have a current version number.
In contrast, our focus on behavior-based testing considers the interaction of configuration settings, service availability, backported patches and other factors that may completely secure a host. This holistic approach results in:
- Near zero false positives - if beSECURE reports a vulnerability, it truly is relevant
- Accurate prioritization - your staff can address the highest risk vulnerabilities with certainty
- Actionable results - succinct reports deliver accurate results with valuable mitigation recommendations
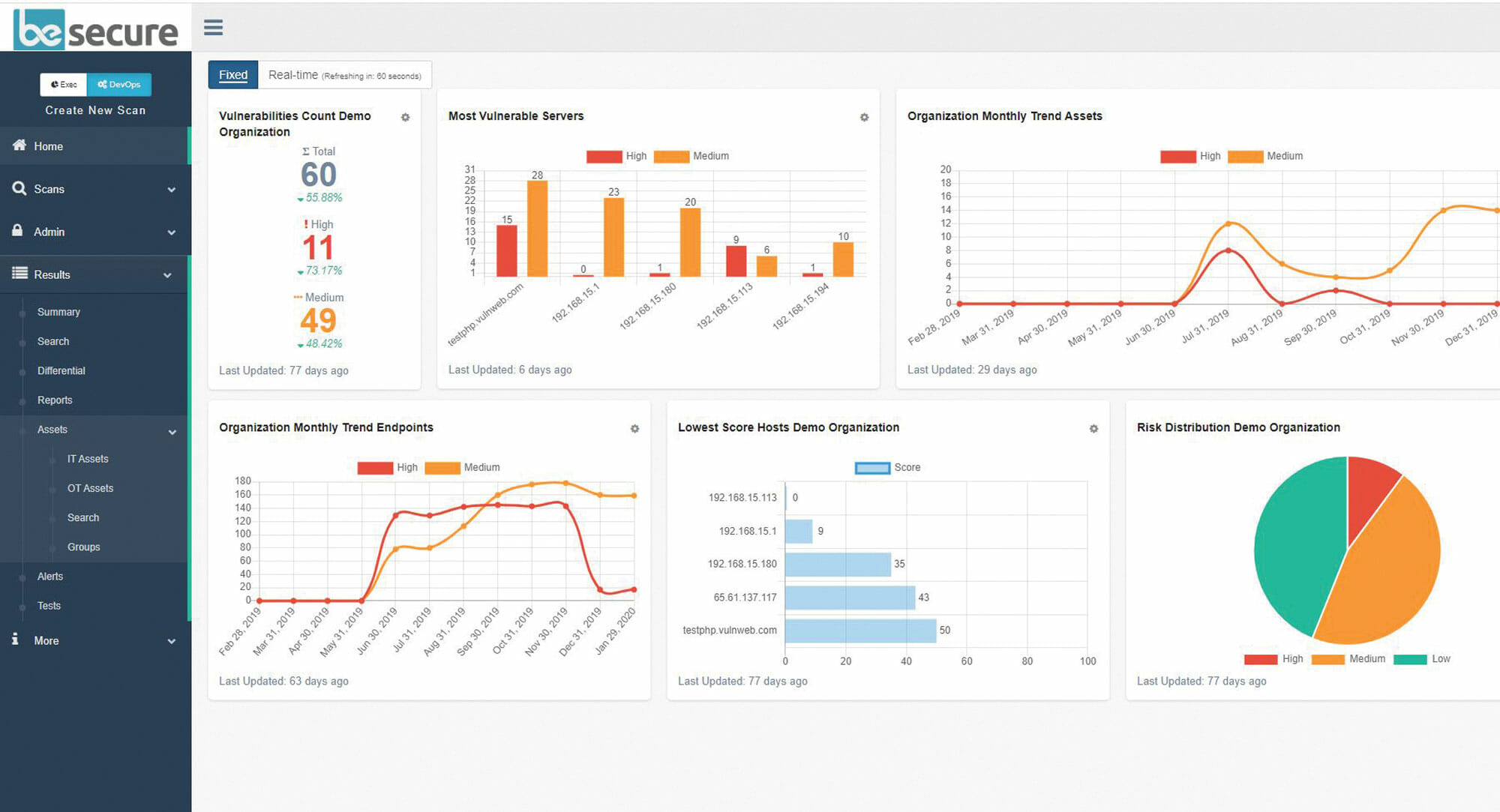
Flexible deployment options for any company, any industry
The beSECURE product line has a solution for any IT scenario. Whichever service you select includes every feature available - there are no extra cost options, modules or professional services required to implement.
In addition to scanning the entire corporate network, also test any Software as a Service, Infrastructure as a Service or Platform as a Service. The beSECURE product portfolio covers everything your network has running now and whatever may be added to it in the future
Easy to use - fastest time to value
Consider the "time to value" of any new VAM. If value isn't there immediately - the solution is unlikely to deliver ROI in the long run.
beSECURE , the Automated Vulnerability Detection System includes:
- Easy setup and maintenance - ensuring best use of time and expertise.
- Detection of vulnerabilities previously missed - get continuous improvement.
- No professional services needed for installation or operation.
- Licensing optimized for scanning very large network ranges
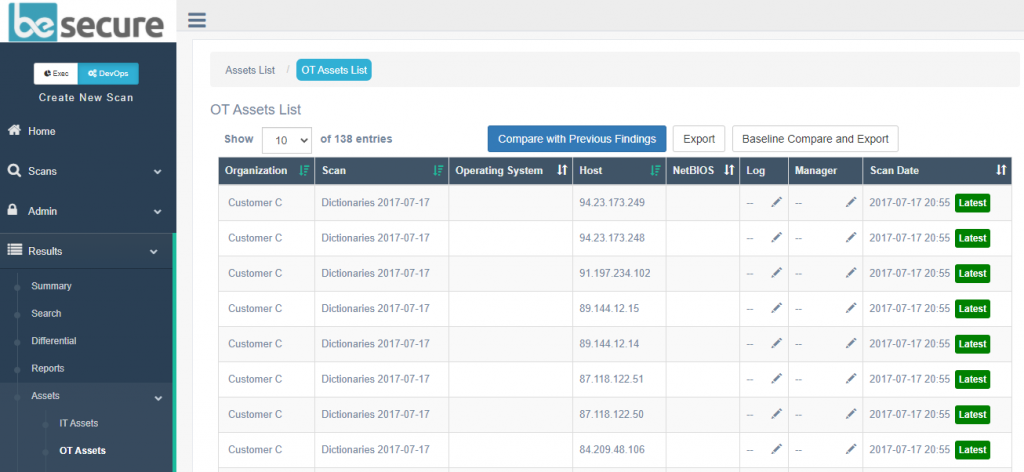
Integration for all your requirements
It takes people, process, and technology working together to protect your data. In this integrated security world, VAM must play well with others.
Every beSECURE system includes, at no extra cost:
Flexible bi-directional APIs
- SIEM integration - for on-demand scanning and reporting
Ticketing integration - for efficient workflow
- Report integration - deliver test results anywhere
Fundamental business capabilities:
- Compliance reports - including PCI, GDPR, HIPAA, ISO, SOX and NERC-CIP
- Persona focused reporting - delivers relevant reports to executives, managers and administrators - including GDPR reports.
- Web application scanning - for vulnerability free web based services