The website uses cookies to deliver services in accordance with the Cookies Policy. You can define the conditions for storing or accessing the cookie mechanism in your browser.
Dynamic security testing of applications
beSTORM® performs comprehensive analysis, uncovering vulnerabilities both in the finished product and during the development process.
beSTORM presents a new approach to security auditing.
Most security holes found in products and applications today can be detected automatically. By using an automated attack tool that tries virtually all different combinations of attacks, with the ability to detect certain application anomalies and indicate a successful attack, security vulnerabilities can be found with almost no user intervention.
beSTORM is both a fuzzy framework and a protocol fuzzer. It comes with a predefined set of protocol "modules", each of which contains a complete description of an RFC-compliant protocol.
beSTORM
- tries to create all (different) protocol combinations and sends them to the target. Since every other combination is "fuzzy"
- covers the entire protocol space completely
.jpg)
Since this can result in millions and sometimes even hundreds of millions of combinations, beSTORM supports parallelism in several ways - by being multi-threaded and allowing the attack to be distributed. It is also very efficient in the ways it carries out attacks, allowing you to limit the attack speed so as not to "choke" the target.
If you would like to extend the protocol module or build a test module for your own protocol, beSTORM comes with a module or module building tool that includes very useful "auto-learning" features that tries to deduce the protocol format from network sniffing or by analyzing captured packets. beSTORM uses various statistical analysis features to try to "guess" what the packet format is.
In addition to network fuzzing, it has file fuzzing and DLL/ActiveX library fuzzing.
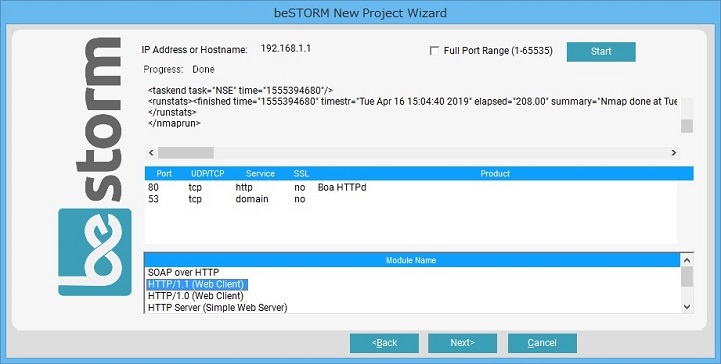
Finally, to complete the package, beSTORM comes with a "checker" component that can be attached to the application under test and monitor it for memory leaks, buffer overflows, etc. This identifies the problem and helps catch "subtle" vulnerabilities that do not cause the application to crash, but lead to memory overruns that might otherwise go unnoticed.
"Controller" communicates with the beSTORM console using an open API that allows you to build dedicated controllers for your own platforms.
When a problem is detected, beSTORM can generate a Perl script that reproduces the problem and can be used by the QA team to further investigate the issue.
Confirming known and discovering unknown vulnerabilities
Dynamic testing tools typically execute a specific set of test cases, perhaps thousands or at best tens of thousands. beSTORM typically executes millions and can deliver billions of attack combinations, filling the entire possible test realm:
- Testing protocols, files, hardware, DLLs, APIs and more
- Certification of powerful, robust attack resilience
- Show engineers what happened - provide specific input that caused the undesired effect - often crashing the application
- Verify the code fix as complete - repeatable tests document success/failure
IT solutions
Test a product
On local martkets Bakotech Group operates through a well-established partner network, including over 1,000 active dealers. Key IT-integrators and are involved in the realization of large-scale projects concerning implementing solutions for end-customers from various segments of business. Bakotech's business strategy is True Value Added Distribution or in other words - project oriented distribution.
We are providing our partners with a wide range of services such as PR, co-marketing activities, pre post-sales support, trainings for partners and end-customers, PoC, PoV, solution consulting, implementation support and technical support.
Contact Us
Bakotech Sp. z o.o.
Dane firmy
VAT ID 6762466740
REGON 122894922
KRS 0000467615
Kontakt
ph. +48 12 340 90 30













