The website uses cookies to deliver services in accordance with the Cookies Policy. You can define the conditions for storing or accessing the cookie mechanism in your browser.
Development and new opportunities powered by AI – help or threat for SOC analysts?
 06.03.2024
06.03.2024The use of AI in cybersecurity tools is becoming more and more common, and the example of the development of Energy Logserver perfectly illustrates how advanced technologies can revolutionize the work of analysts in the field of information security. These tools not only improve threat detection, but also increase the effectiveness and speed of response to cyber incidents
.png)
Can the work of SOC analysts be replaced?
SOC (Security Operations Center) analysts play a key role in monitoring and responding to cyber threats. Their work involves continuous analysis of events in the IT infrastructure in order to detect anomalies and potential attacks. Traditionally, analysts relied on their experience and intuition to quickly spot differences in the events they were analyzing, but this was limited to the information they could see on the screen.
Currently, they are facing increasing challenges caused not only by the increasing number of attacks, but also by their sophistry. Traditional log analysis methods are time-consuming and can miss subtle anomalies that are often early indicators of attacks. Therefore, the development of tools using AI to automate and improve analysis processes is crucial to increase the effectiveness of threat detection.
Empowered AI - New Possibilities
The development of the Empowered AI module in Energy Logserver is a breakthrough in the approach to log analysis and anomaly detection. Using machine learning algorithms, this tool can analyze huge amounts of data in real time, detecting anomalies that could escape the attention of a human operator. These algorithms learn from log history, constantly improving their ability to identify potential threats.
Artificial intelligence makes it possible to replicate the thought process of a SOC analyst, but with greater accuracy and speed. The newly developed "Anomaly Detection - Text" rule analyzes each log, using mathematical functions to assess the probability of each word occurring in the analyzed set. Thanks to this, even the rarest words that may indicate an attack attempt are quickly detected and analyzed.
Usage Example
Let's see an example of one of the caught entries:
Text
205.210.31.32 - - [20/Feb/2024:14:00:37 +0100] "GET / HTTP/1.1" 301 224 "-" "Expanse, a Palo Alto Networks company, searches across the global IPv4 space multiple times per day to identify customers' presences on the Internet. If you would like to be excluded from our scans, please send IP addresses/domains to: scaninfo@paloaltonetworks.com" **0.125**
Rare words
['would', 'ipv4', 'global', 'please', 'across', 'networks', 'company', 'per', 'internet', 'times', '0.125', 'the', ' from', 'a', 'if', 'addresses/domains', 'multiple', '39', 'scans', 'expanse', 'space', 'alto', 'excluded', 'palo', ' send', 'scaninfo@paloaltonetworks.com', 'searches', 'day', 'you', '205.210.31.32', 'identify', 'our', 'presences', 'ip', 'customers']
These detections make up the following calculations:
Rare words: 35
Single word anomaly points: 10,155
Entire logo anomaly points: 330,001
Number of occurrences of the indicated logo as a whole: 1
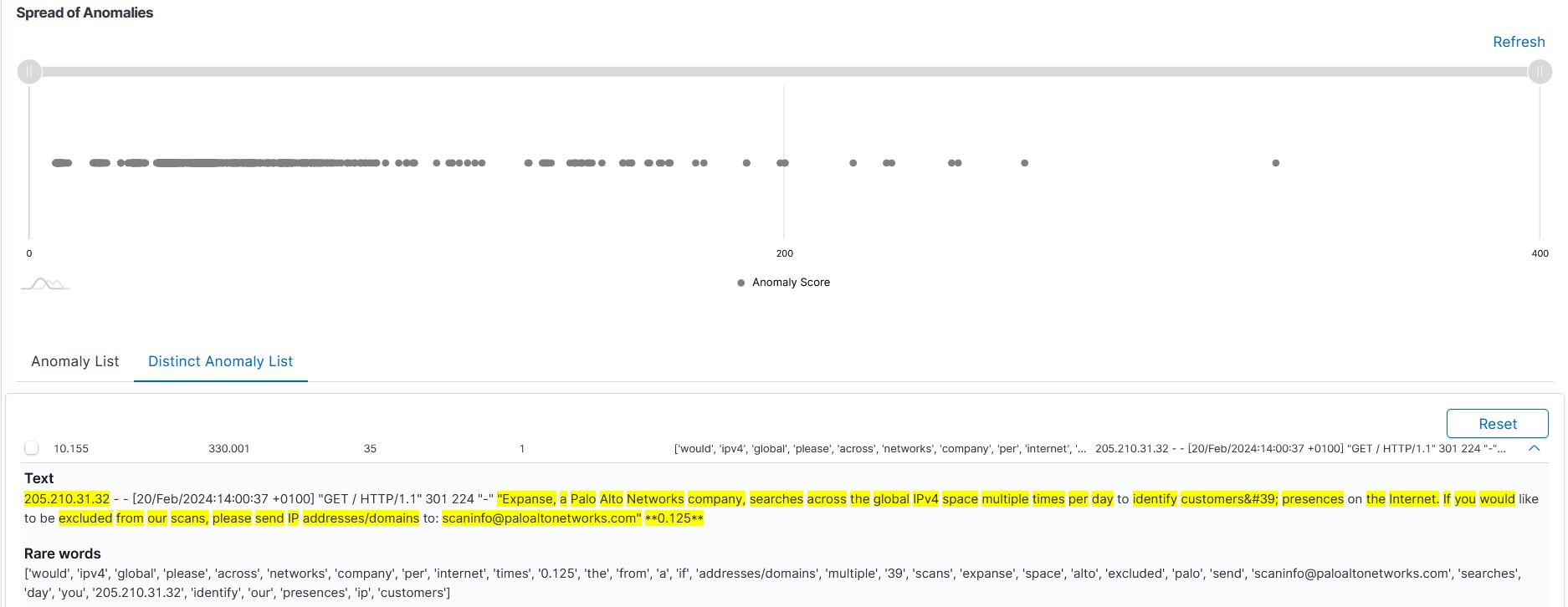
Analysis of a specific log entry showed how AI can effectively detect and evaluate logs in terms of word sparsity and total anomaly score. In the case of the Palo Alto Networks logo, even though the entry turned out to be harmless, the system was able to identify and assess a potential anomaly thanks to advanced AI algorithms.
Future Directions of Development
Further development of Energy Logserver looks promising, with plans to introduce features such as Empowered AI rule scheduling, anomaly score alerting, real time anomaly score, and building a library of models for various data sources. The Empowered AI rule schedule will allow you to automate analysis processes to an even greater extent, and the anomaly score-based alerting function will enable you to be informed about potential threats faster. Real time anomaly score, in turn, will allow for ongoing monitoring of the infrastructure, ensuring immediate response to anomalies.
These upcoming features are intended not only to improve threat detection and response processes, but also to create a community of users who will share and use saved models.
Conclusions
Integrating AI into cybersecurity tools like Energy Logserver is changing the work paradigm for SOC analysts, enabling them to detect threats faster and more precisely. Thanks to advanced algorithms and artificial intelligence, it becomes possible to predict and prevent incidents before they negatively impact the organization's infrastructure. The development of these technologies is key to increasing overall cyber resilience in a dynamically changing threat environment.
To learn more about SIEM and SOAR technology and the possibilities of using AI in Energy Logserver solutions, please contact us. We will be happy to answer any questions and provide the necessary information.
Contact Us
Bakotech Sp. z o.o.
Dane firmy
VAT ID 6762466740
REGON 122894922
KRS 0000467615
Kontakt
ph. +48 12 340 90 30
















