The website uses cookies to deliver services in accordance with the Cookies Policy. You can define the conditions for storing or accessing the cookie mechanism in your browser.

Thunder TPS
A10 Thunder TPS® (Threat Protection System) is the world's most powerful DDoS protection solution, leading the industry in accuracy, intelligent automation, scalability and performance.
New threat vectors have changed the scope, intensity and complexity of the options available to attackers. Today's attacks have evolved and now include DDoS toolkits, weaponized IoT devices, online DDoS services, and more. Established solutions that rely on ineffective signature-based IPS or just rate-limiting traffic are no longer sufficient. Thunder TPS scales to protect against IoT DDoS and traditional zombie botnets and detects DDoS attacks through high-resolution packet analysis or flow logs from edge routers and switches. Unlike legacy DDoS defense products, A10 Networks' DDoS defense includes detection capabilities in key network elements Platforms and Services Thunder TPS Physical Appliance Thunder TPS Virtual Appliance DSIRT DDoS Specialized support including A10 Thunder® ADC, CGN and CFW. These features provide the context, packet-level granularity and visibility needed to thwart today's sophisticated attacks. One-DDoS Protection detectors work in concert with A10 Networks' centralized management system andGalaxy® and Thunder TPS for centralized mitigation that provides fast and cost-effective DDoS resiliency.
Full Spectrum DDoS Protection for Service Availability
A10 Thunder TPS detects and mitigates broad levels of attacks, even if multiple attacks hit the network simultaneously.
Features
Complete Solution For Flexible Deployments
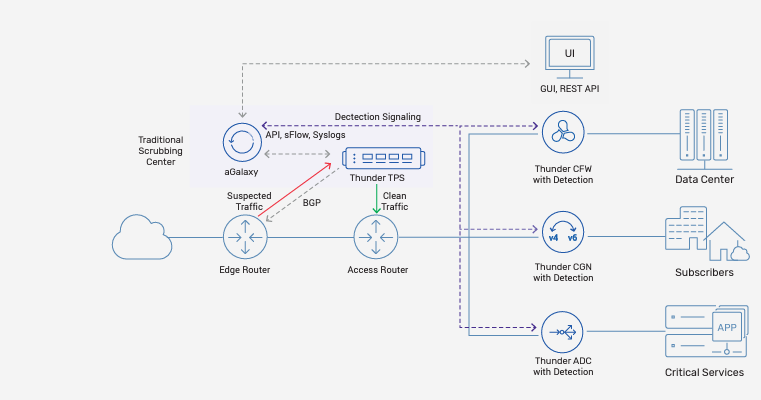
Thunder TPS DDoS solutions provides a complete solution for DDoS defenses in proactive always-on or on-demand reactive modes to meet their business objectives. Thunder TPS can be deployed in L2 or L3 inpath modes with full IPv4 and IPv6 support. On-demand reactive DDoS detection is facilitated with the collection and analysis of exported flow data records from routers and switches. The Thunder TPS detector applies always-on adaptive learning to build peacetime profiles for protected servers and services, based on 15 flow record traffic indicators to spot anomalous behavior. When an attack is detected, aGalaxy instructs Thunder TPS to initiate a BGP route redirection for the suspicious traffic. Then TPS applies the appropriate countermeasures using a progressive auto mitigation level escalation technique before delivering the clean traffic to the intended destination.
Multi-Vector Attack Protection
Detect and mitigate DDoS attacks of many types, including volumetric, protocol, or resource attacks; application-level attacks; or IoTbased attacks. Hardware acceleration offloads the CPUs and makes Thunder TPS particularly adept to deal with simultaneous multi-vector attacks.
Hybrid DDoS Protection
Thunder TPS on-premise protection works in concert with 3rd party cloud-based DDoS scrubbing service to provide full-spectrum protection against attacks of any type. When attacks grow beyond an organization’s bandwidth capacity, cloud mitigation can be initiated automatically by Thunder TPS using BGP based signaling, API, and scripting etc.
ZAP Zero-Day Automated Protection
The ZAP engine utilizes heuristic and machine learning automatically discover mitigation filters without advanced configuration or manual intervention. ZAP speeds the response time against increasingly sophisticated multi-vector attacks while minimizing downtime and errors and lower operating costs.
One-DDoS Protection Layered, Distributed Detection
One-DDoS Protection provides the freshest approach to full-spectrum DDoS defense, placing detection capabilities across key network elements closest to the targeted elements of the infrastructure. This provides the context, packet level granularity, and visibility needed to thwart today’s sophisticated targeted attacks. A10 Thunder ADC, CGN, and CFW with integrated DDoS detectors work in concert with Thunder TPS’ edge f low-based detection and centralized mitigation to enable full spectrum DDoS resilience.
Benefits
- Maintain Service Availability
- Defeat Growing Attacks
- Scalable Protection
- Deploy Wartime Support
- Reduce Security OPEX
IT solutions

Test a product
On local martkets Bakotech Group operates through a well-established partner network, including over 1,000 active dealers. Key IT-integrators and are involved in the realization of large-scale projects concerning implementing solutions for end-customers from various segments of business. Bakotech's business strategy is True Value Added Distribution or in other words - project oriented distribution.
We are providing our partners with a wide range of services such as PR, co-marketing activities, pre post-sales support, trainings for partners and end-customers, PoC, PoV, solution consulting, implementation support and technical support.
Contact Us
Bakotech Sp. z o.o.
Dane firmy
VAT ID 6762466740
REGON 122894922
KRS 0000467615
Kontakt
ph. +48 12 340 90 30












