The website uses cookies to deliver services in accordance with the Cookies Policy. You can define the conditions for storing or accessing the cookie mechanism in your browser.
Secure sensitive data used by employees. Secure and track every file, on every device. With just one click, secure your documents, presentations, videos or images with AES 256-bit encryption and granular access policies that come with the file.
With a simple, consistent interface on each Vera promotes secure behavior and and discourages your employees from choosing risky and insecure solutions.
- Report which internal users can access sensitive files and any failed attempts.
- Control sensitive files at any time, even after a file has been emailed, shared, or is on a terminated user's device.
- Control sensitive files in basic applications (e.g., preview, edit, print, copy/paste, watermark).
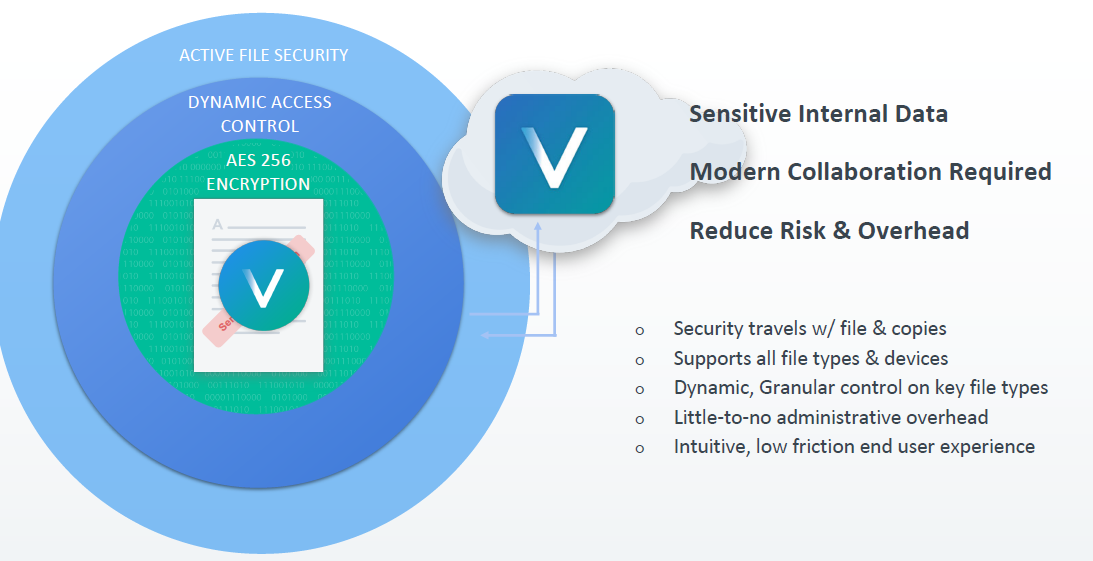
Active file protection
File content is always safe, even when in use:
- Apply AES-256 encryption to any file type to prevent access to sensitive data by unknown parties.
- Granular insight and centralized control; understand how your content is being used, by whom, and proactively investigate unauthorized access attempts.
- Policies can be based on multiple pre-defined parameters such as file location, name, type, security, sender, recipient, group, or other pre-existing permission structures.
Take advantage of modern collaboration in a secure way
Box, Dropbox, and SharePoint enable improved productivity and convenience for knowledge workers and make it much easier to share information with external users.
- Control access to confidential files even after they have been shared with external users via cloud collaboration tools, email, or other means.
- Standardize on sanctioned cloud collaboration tools without the risk of vendor access to confidential files.
- Employees and external users can securely collaborate using cloud applications.
File Activity Tracking
Easy to use web portal for extensive in-product auditing.
- File access, duration, location, activities
- User login, file access and activity
- Device type, information and access
- System events (administrator and user actions)
- Syslog support
- CSV export
Any device, any location
A configurable rules-based engine that provides automated security and access control access control for:
- Local desktop folders,
- Box, Dropbox, network shares, SharePoint repositories and OneDrive repositories,
- Legacy access control and mapped permissions,
- Email attachments.
Flexible deployment options
Increase overall file data security by integrating Vera with your own applications:
- SaaS deployment model
- Allows for a hybrid model where Vera infrastructure for file protection/viewing and key management can be deployed on-premise
- VPC option in AWS for customers with high security requirements
- On-Premise for federal and military services
- SDK allows integration with third-party applications third-party applications such as web applications, DLP, classification and DMS.
- Integration with identity management solutions such as Okta, Google, AD, LDAP, etc.
- Integration with existing file sharing solutions such as Box, Dropbox, SMB, SharePoint, and OneDrive
- Configurable to work with enterprise email archiving solutions
Mitigating compliance risks
Regulators continue to implement rules and penalties related to privacy and security. Organizations must achieve a state of continuous compliance while enabling business operations,:
- Files containing PII, PCI or PHI can only be accessed by authorized users
- An audit trail of all successful and failed attempts to access sensitive files
- Ability to revoke access to sensitive files, even if they are accessed by unauthorized users
- Your teams have the ability to use our SDK and REST APIs to encrypt, track, and revoke file access
Test a product
On local martkets Bakotech Group operates through a well-established partner network, including over 1,000 active dealers. Key IT-integrators and are involved in the realization of large-scale projects concerning implementing solutions for end-customers from various segments of business. Bakotech's business strategy is True Value Added Distribution or in other words - project oriented distribution.
We are providing our partners with a wide range of services such as PR, co-marketing activities, pre post-sales support, trainings for partners and end-customers, PoC, PoV, solution consulting, implementation support and technical support.
Contact Us
Bakotech Sp. z o.o.
Dane firmy
VAT ID 6762466740
REGON 122894922
KRS 0000467615
Kontakt
ph. +48 12 340 90 30













